Tool Overview:
Canopy
Overview
Based: United States
Contact: https://www.canopyco.io/contact
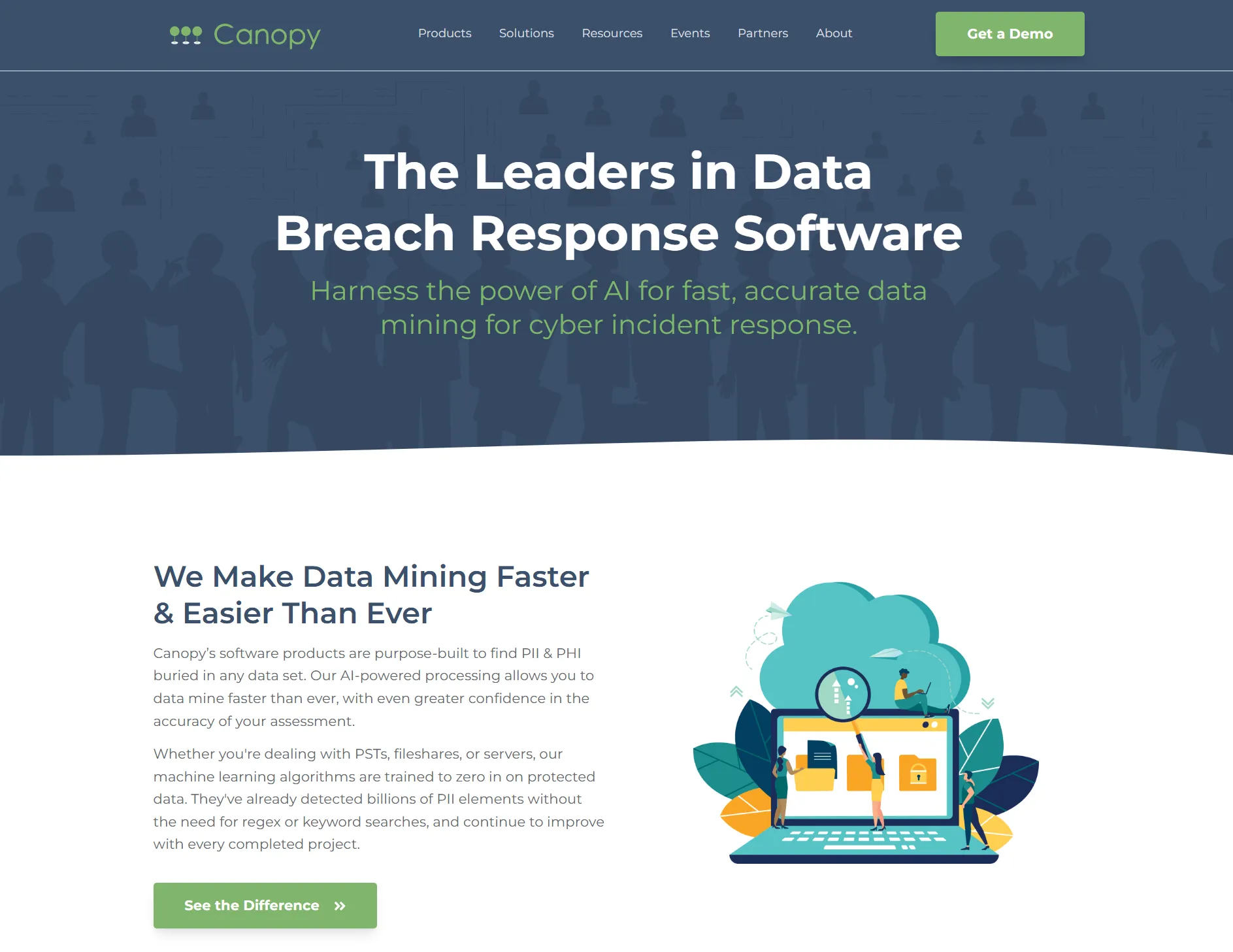
About Canopy
Canopy is a data breach response software platform specifically designed for detecting and analyzing personally identifiable information (PII) and protected health information (PHI) in compromised data sets. The platform processes breached data using machine learning algorithms to identify sensitive information across multiple jurisdictions and regulatory frameworks including GDPR, CCPA, HIPAA, and FERPA. The software runs in a virtual private cloud environment and maintains ISO 27001 certification.
What does Canopy do?
The platform employs hundreds of machine learning models, each trained to detect specific types of sensitive data such as social security numbers, credit card numbers, religious affiliations, and diagnostic codes. These models process incoming data sets and automatically generate an Impact Assessment Report within 24-72 hours, significantly faster than traditional manual assessments which typically take 1-2 weeks. The software encrypts data both at rest and in transit, with data residing in virtual private clouds within the required jurisdiction.
Canopy's workflow consists of four main phases: initial processing and impact assessment, data mining to identify documents containing PII/PHI, human review of flagged documents, and entity management for consolidating notification lists. During the review phase, the software highlights potentially sensitive information for human reviewers to verify and link to specific individuals. The platform includes features for handling complex data types, such as the ability to map and extract protected information from spreadsheets and tables embedded in emails or Word documents.
What makes Canopy different?
A key differentiator of Canopy from traditional eDiscovery tools is its purpose-built focus on PII and PHI detection. While eDiscovery software aims to identify legally relevant documents for corporate disputes or investigations, Canopy specifically targets sensitive personal data for breach notification purposes. The platform includes specialized features like automated column matching for spreadsheets, foreign language detection across 60 languages, and image classification to distinguish between documents containing sensitive information versus standard business graphics.
The software's entity management capabilities help reduce duplicate entries in notification lists through automatic merging of identical entities and suggestion of near-duplicate entries. This helps streamline the process of creating consolidated notification lists for breach reporting. Administrative features include granular user permissions, document batching tools, and on-demand progress reporting through the Review Metrics Report.
Use cases and industries
Canopy serves multiple stakeholders in the data breach response process, including digital forensics and incident response (DFIR) teams, law firms, and legal service providers. The platform has been used to process various breach scenarios, from 50 GB business email compromises to multi-terabyte ransomware attacks. In one documented case, the software processed 76.77 GB of compromised PSTs containing over 829,000 documents across 15 PII categories.
The software supports privacy audits for proactive risk management, allowing organizations to analyze their data repositories for sensitive information before breaches occur. This includes analyzing employee email inboxes and file shares to understand how PII is being handled internally. Healthcare organizations, technology companies, and other enterprises handling sensitive data have implemented Canopy for both reactive breach response and proactive privacy management.
Pricing
Pricing information not available.