Tool Overview:
Pointsharp
Overview
Based: Sweden
Contact: https://www.pointsharp.com/en/contact
About Pointsharp
Pointsharp is a European cybersecurity company that provides identity and access management solutions for organizations seeking to secure their digital workplaces. The company offers a suite of products designed to protect data, manage identities, and control access across both on-premises and cloud environments. Their solutions address the growing challenges of securing hybrid infrastructures while maintaining user-friendly access methods.
What does Pointsharp do?
The platform centers on three core capabilities: secure application access, identity management, and secure file transfer. The Access Gateway enables organizations to publish applications securely with multi-factor authentication and single sign-on capabilities, supporting both cloud and on-premises applications. For identity management, Pointsharp provides certificate-based authentication using hardware tokens like YubiKeys and smart cards, along with mobile tokens and soft tokens for flexible login options.
A distinctive component of Pointsharp's offering is its Exchange Protection service, which provides multi-factor authentication for on-premises Exchange servers, securing access and synchronization even from Outlook and mobile devices. The platform includes Cryptshare, a secure file transfer solution that integrates with email systems to facilitate the exchange of sensitive information and large files while maintaining compliance with regulatory requirements.
The identity provider (IdP) serves as the foundation of Pointsharp's identity and access management solution, enabling centralized authentication across applications. This component communicates with directory services such as Active Directory, Entra ID (formerly Azure AD), and LDAP to verify user identities and access rights. The system supports single sign-on and single sign-off functionality, streamlining the user experience while maintaining security controls.
What makes Pointsharp different?
Pointsharp's approach to security emphasizes user experience alongside robust protection measures. The platform incorporates self-service capabilities for password resets and security token enrollment, reducing IT department workload while maintaining security standards. The solution provides centralized control over security policies, allowing organizations to specify which types of authentication tokens are permitted and whether they should be combined with biometric or PIN verification.
The platform's PKI-as-a-service offering distinguishes itself by providing cloud-based certificate management without requiring organizations to build and maintain their own PKI infrastructure. This service builds on two decades of experience serving high-security environments, making enterprise-grade PKI capabilities accessible to organizations that may lack the resources to develop such infrastructure internally.
Use cases and industries
Pointsharp addresses several specific use cases in modern enterprise environments. The platform enables secure remote work without requiring VPN connections, supports BYOD initiatives, and helps prevent shadow IT through controlled file sharing capabilities. The solution is particularly relevant for organizations with hybrid infrastructure environments that need to secure both legacy applications and cloud services.
The platform serves organizations dealing with sensitive data transfer requirements, particularly those needing to exchange large files or confidential information with external parties while maintaining regulatory compliance. The implementation of certificate-based authentication and hardware token support makes it suitable for environments with stringent security requirements, such as those subject to NIS2 compliance obligations.
For IT departments, Pointsharp provides tools for managing the complete lifecycle of security tokens and certificates, including self-service enrollment processes that reduce administrative overhead. The platform supports multiple operating systems including Windows, macOS, and Linux, as well as various mobile devices, making it applicable for organizations with diverse technology environments.
Pricing
Pricing information not available.
Product Screenshots
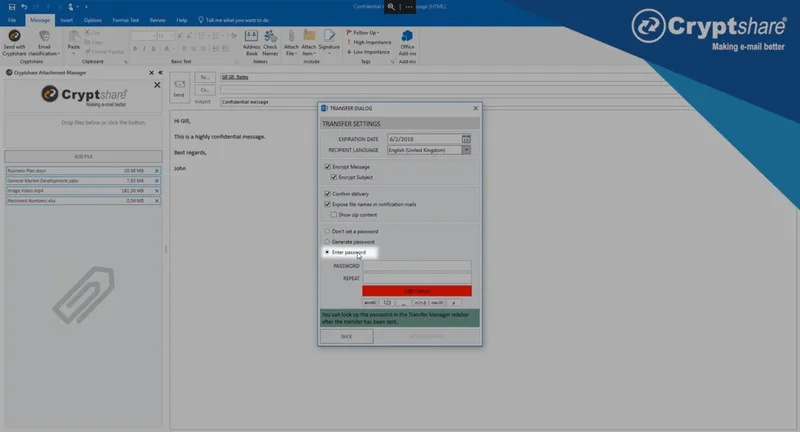 Cryptshare screenshot from Pointsharp onboarding website. Source: https://www.cryptshare.express/en/onboarding
Cryptshare screenshot from Pointsharp onboarding website. Source: https://www.cryptshare.express/en/onboarding